Cloud Storage HMAC Keys: A Deep Dive for the Modern Cloud Architect and Engineer

As a Google Cloud systems architect and cloud engineer, you are at the forefront of designing and building secure, scalable, and resilient cloud infrastructure. A critical, yet often complex, aspect of this is managing access to cloud storage. While Google Cloud offers a robust suite of identity and access management (IAM) tools, there are specific scenarios where a different approach to authentication is required. This is where Cloud Storage HMAC (Hash-based Message Authentication Code) keys come into play.
This blog post will provide a comprehensive exploration of Cloud Storage HMAC keys. We will delve into their advantages and disadvantages, compare them with the robust capabilities of Cloud Key Management Service (Cloud KMS), and outline the various key management strategies available in Google Cloud. By the end, you will have a clear understanding of when to leverage HMAC keys and how to manage them effectively, ensuring the security and integrity of your data.
Demystifying Cloud Storage HMAC Keys
At its core, an HMAC key is a credential used to authenticate requests to Cloud Storage. It consists of an access ID and a secret, which are used to generate a cryptographic signature for each request. This signature validates the authenticity and integrity of the request, ensuring it hasn't been tampered with in transit and that it originates from a trusted source.
The primary use case for HMAC keys in Google Cloud is to provide interoperability with other cloud storage services, most notably Amazon S3. Many existing tools and libraries are built to work with the S3 API, which uses a similar HMAC-based authentication mechanism. By using HMAC keys, you can seamlessly migrate data from other cloud providers to Google Cloud Storage or use your existing S3-compatible tools without significant code changes.
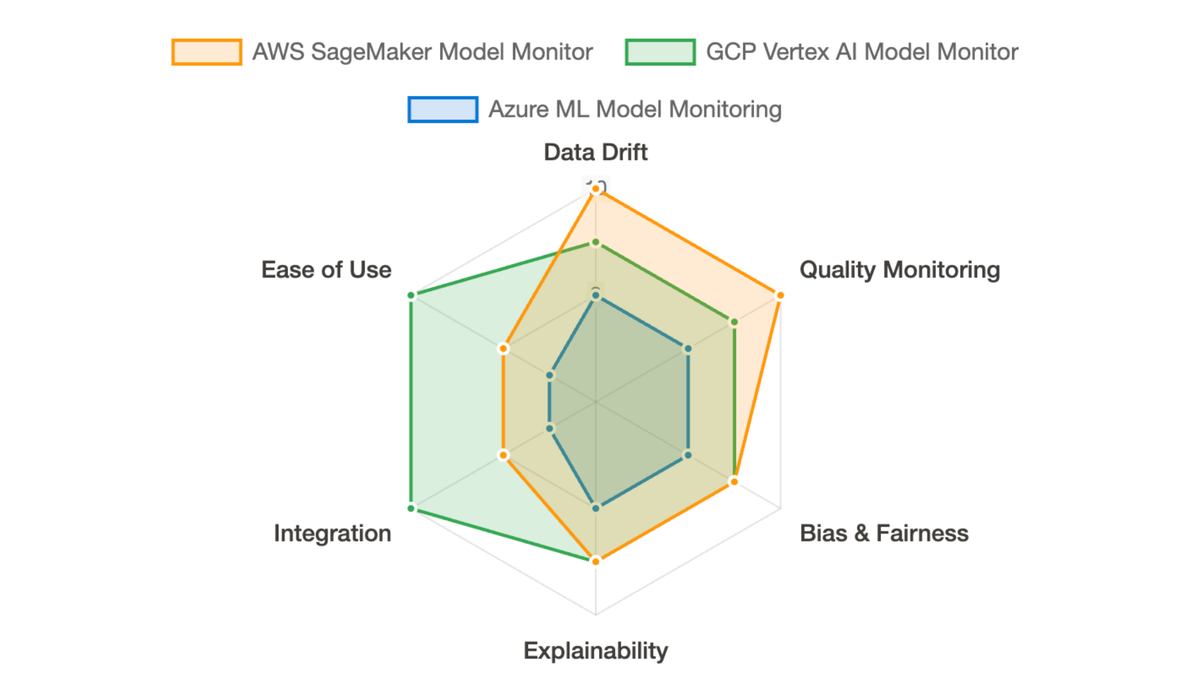
Cloud KMS vs HMAC Keys
While HMAC keys offer a convenient solution for interoperability, it's crucial to understand their trade-offs, especially when compared to Google Cloud's premier key management solution, Cloud KMS.
Primary Use Case
HMAC: Interoperability with S3-compatible tools and services.
KMS: Centralized management of cryptographic keys for Google Cloud services.
Security
HMAC: Relies on the security of the access ID and secret. If compromised, they grant direct access to storage.
KMS: Provides a robust hierarchy of keys with granular access controls through IAM. Keys can be software-backed, hardware-backed (HSM), or external.
Management
HMAC: Manually created, rotated, and deleted. Responsibility for secure storage of the secret lies entirely with the user.
KMS: Centralized management console and API. Automated key rotation schedules. Detailed audit logging of all key usage.
Granularity
HMAC: Associated with a service account or user account, granting the permissions of that account.
KMS: Fine-grained permissions can be applied to individual keys, controlling who can use them and for what purpose.
Auditability
HMAC: Limited native audit logging for HMAC key creation and usage.
KMS: Comprehensive Cloud Audit Logs for all administrative actions and cryptographic operations.
Cost
HMAC: No direct cost for the keys themselves.
KMS: Pricing is based on the number of key versions, protection level (software, HSM, external), and cryptographic operations.
Advantages of HMAC Keys:
- Interoperability: The single most significant advantage is the ability to use a vast ecosystem of S3-compatible tools and libraries with Google Cloud Storage. This simplifies migrations and reduces the need for costly and time-consuming code refactoring.
- Simplicity for Specific Workflows: For straightforward, script-based interactions with Cloud Storage, using HMAC keys can be simpler to implement than setting up service account authentication with OAuth 2.0.
Disadvantages of HMAC Keys:
- Increased Security Responsibility: The security of your storage buckets rests heavily on your ability to protect the HMAC key's secret. Accidental exposure, such as committing it to a public code repository, can have severe consequences.
- Manual Management Overhead: The entire lifecycle of an HMAC key, from creation to rotation and deletion, is a manual process. This can become burdensome at scale and increases the risk of human error.
- Limited Auditability: While you can log the API calls made with an HMAC key, auditing the management of the keys themselves is less straightforward than with Cloud KMS.
- Lack of Granular Control: An HMAC key inherits all the permissions of the associated service or user account. You cannot restrict an HMAC key to perform only a specific subset of actions that the account is authorized for.
The Power of Cloud KMS:
Cloud KMS, on the other hand, is a managed service designed for the secure storage and management of cryptographic keys. It offers a centralized platform to create, use, rotate, and destroy keys, with deep integration into other Google Cloud services. The key benefits of Cloud KMS include:
- Centralized and Granular Control: Manage all your keys from a single pane of glass and apply fine-grained IAM permissions to control who can access and use them.
- Enhanced Security: Cloud KMS provides multiple protection levels, including Hardware Security Module (HSM) and External Key Manager (EKM) options, to meet the most stringent security and compliance requirements.
- Automated Key Rotation: Set up automatic key rotation schedules to reduce the risk of key compromise without manual intervention.
- Comprehensive Auditing: Every action performed on a key is logged in Cloud Audit Logs, providing a clear and immutable record of key usage.
Cloud KMS in a nutshell
A Deeper Dive into Google Cloud Key Management
Beyond the HMAC vs. Cloud KMS discussion, Google Cloud offers a spectrum of key management solutions tailored to different needs. Understanding these options is crucial for designing a robust security posture.
1. Google-Managed Encryption Keys:
This is the default encryption setting for all data at rest in Google Cloud. Google manages the entire key management process, including key creation, rotation, and storage, completely transparently to the user. This is a secure and effortless option for many use cases, but it doesn't offer the customer the ability to directly manage or control the encryption keys.
2. Customer-Managed Encryption Keys (CMEK):
CMEK allows you to have more control over the keys used to protect your data in Google Cloud services like Cloud Storage, BigQuery, and Compute Engine. With CMEK, you use Cloud KMS to create and manage the keys. While Google still performs the cryptographic operations, you control the key's lifecycle and access policies. This is an excellent option for organizations that need to meet specific compliance requirements or want greater control over their data's encryption.
3. Customer-Supplied Encryption Keys (CSEK):
For the highest level of control, CSEK allows you to provide your own encryption keys to Google Cloud. These keys are used to encrypt and decrypt your data, but they are never stored on Google's servers. Instead, you must provide the key with every API request. This approach gives you complete control over your keys but also places the full burden of key management and availability on your shoulders. If you lose your key, you lose your data.
4. Cloud KMS Tiers: Software, HSM, and External
Within Cloud KMS, you have further choices for the protection level of your keys:
- Software: Keys are protected by software-based security measures. This is a cost-effective and highly available option suitable for many workloads.
- Hardware Security Module (HSM): Keys are stored and cryptographic operations are performed within a FIPS 140-2 Level 3 certified HSM. This provides a higher level of security for sensitive workloads.
- External Key Manager (EKM): For organizations with existing on-premises or third-party key management solutions, EKM allows you to use those external keys to protect your data in Google Cloud. This is often a requirement for "bring your own key" (BYOK) strategies.
Making the Right Choice: Practical Use Cases and Scenarios
So, when should you, as a cloud architect or engineer, choose one option over the others?
- Use HMAC Keys when:
- Migrating from AWS S3: You have existing applications or scripts that use the S3 API. HMAC keys provide a seamless transition path.
- Using S3-Compatible Third-Party Tools: Many data management and transfer tools are built for the S3 ecosystem. HMAC keys allow you to leverage these tools with Google Cloud Storage.
- Simple, Scripted Access: For basic command-line or scripted interactions with Cloud Storage where the overhead of OAuth 2.0 is not desired.
- Use Cloud KMS (CMEK) when:
- Meeting Compliance Requirements: Regulations like PCI DSS, HIPAA, and GDPR often require customer-managed encryption keys.
- Centralized Key Management is a Priority: You want a single, unified system for managing all your cryptographic keys across your Google Cloud projects.
- Granular Access Control is Needed: You need to enforce strict separation of duties and control who can use encryption keys for specific purposes.
- Automated Key Rotation is a Must: You want to reduce the operational burden and security risks associated with manual key rotation.
- Use Customer-Supplied Encryption Keys (CSEK) when:
- You Have Extreme Security Requirements: Your organization's security policy dictates that encryption keys must never be stored by the cloud provider.
- You Have an Existing, Robust Key Management Infrastructure: You already have the systems and processes in place to securely manage and provide keys on-demand.
- Stick with Google-Managed Keys when:
- Simplicity and Ease of Use are Paramount: You trust Google's robust security posture and don't have specific compliance or control requirements that necessitate customer-managed keys.
Best Practices for HMAC Key Management
If you determine that HMAC keys are the right choice for your use case, it's imperative to follow these best practices to mitigate the inherent security risks:
- Use Service Accounts: Whenever possible, associate HMAC keys with dedicated service accounts rather than user accounts. This decouples the key's lifecycle from an individual user's employment status and allows for more granular IAM permissions on the service account.
- Principle of Least Privilege: Grant the associated service account only the minimum permissions required to perform its intended function. For example, if a tool only needs to read data, assign the
Storage Object Viewerrole, notStorage Object Admin. - Regular Rotation: Establish a regular schedule for rotating your HMAC keys. This limits the window of opportunity for a compromised key to be exploited.
- Secure Storage of Secrets: The HMAC secret is the "keys to the kingdom." Never hardcode it in your source code, and avoid storing it in plain text. Use a secure secret management solution like Google Secret Manager to store and access HMAC secrets.
- Monitor for Usage: While native auditing is limited, you can monitor the API calls made using the HMAC key's access ID in your Cloud Storage access logs. Look for any anomalous activity.
- Delete Unused Keys: Promptly delete any HMAC keys that are no longer needed to reduce your attack surface.
Impersonation and service account keys
What about using service account keys to impersonate a service account from outside of Google Cloud? Check out this video from Google Cloud for a summary of the options:
Service account keys and impersonation in Google Cloud
A Deliberate Approach to Key Management
In the dynamic world of cloud computing, a one-size-fits-all approach to security is rarely effective. As a Google Cloud systems architect or cloud engineer, your role is to understand the nuances of the available tools and make informed decisions that align with your organization's security posture, compliance requirements, and operational capabilities.
Cloud Storage HMAC keys are a valuable tool in your arsenal, particularly for ensuring interoperability with the broader cloud ecosystem. However, their convenience comes with a significant responsibility for secure management. For most other use cases, the robust features, centralized control, and enhanced security of Cloud KMS make it the superior choice for managing your cryptographic keys in Google Cloud.
By carefully evaluating your specific needs and following the best practices outlined in this post, you can design and implement a key management strategy that is both secure and effective, enabling you to build with confidence on Google Cloud.
Read more: